The Ultimate Guide To Risk Management Enterprise
The 8-Second Trick For Risk Management Enterprise
Table of ContentsSome Known Facts About Risk Management Enterprise.Little Known Facts About Risk Management Enterprise.Not known Factual Statements About Risk Management Enterprise
Control who can check out or modify these elements by setting particular accessibility civil liberties for specific users, ensuring information security and tailored usability. Permits users to customize their user interface by choosing and setting up crucial data elements. Provides a customized experience by allowing customization of where and how information aspects are shown.It permits access to real-time incorporated data instantaneously. Risk Management Enterprise. Likewise, this assists eliminate wasted time on hand-operated record compilation. Centers can use comprehensive data intelligence for quicker and extra informed decision-making. It permits the automatic development of stakeholder records for individuals or teams. Enables prompt decision-making and decreases delays brought on by outdated info.
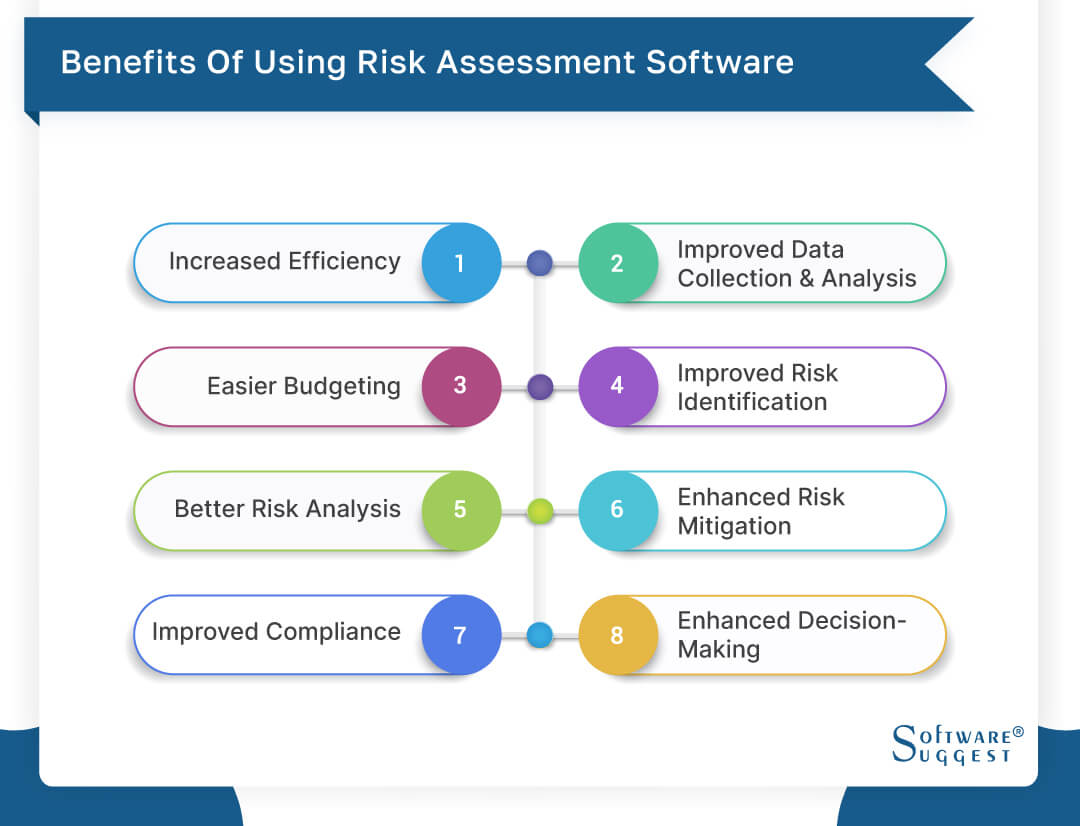
Diligent is a risk administration software that enables enhancing performance, and increases development. It also aids keep an eye on dangers with ERM software application that includes incorporated analytics and adapts to your service needs. This software application includes numerous useful attributes. Below we have highlighted one of the most important ones. So, inspect them out.
The Best Strategy To Use For Risk Management Enterprise
It likewise offers one-click reports. In addition, it offers your leadership and board the real-time insights they require. Simplifies the process of accumulating threat information from different parts of the organization. Risk Management Enterprise. It permits for simple personalization of reports and storyboards. Provides management and the board with real-time risk understandings. Use ACL's advanced analytics to spot threat patterns and forecast threats.
This permits companies to catch risk insights and red flags in the third-party vendor's safety and security record. Makes it possible for business to record and record threat insights and red flags in third-party vendor protection reports.
Recognizing risks beforehand assists a facility prepare for audits. It additionally lowers risk with streamlined compliance and danger monitoring. Due to this centers will not need to handle various systems for danger monitoring. The customers of Hyperproof can streamline threat monitoring in one location. It can assist gather and track all your dangers in the Hyperproof danger register.
It ensures that whatever is organized and easily accessible for auditors. Makes use of automation to maintain evidence up-to-date while minimizing hand-operated effort. It offers quick accessibility to essential information and documentation. This ensures the safety and more information security of Active evidence instances by enabling multi-factor authentication (MFA) making use of authenticator applications such as Google Authenticator, Microsoft Authenticator, or Authy.
The smart Trick of Risk Management Enterprise That Nobody is Talking About
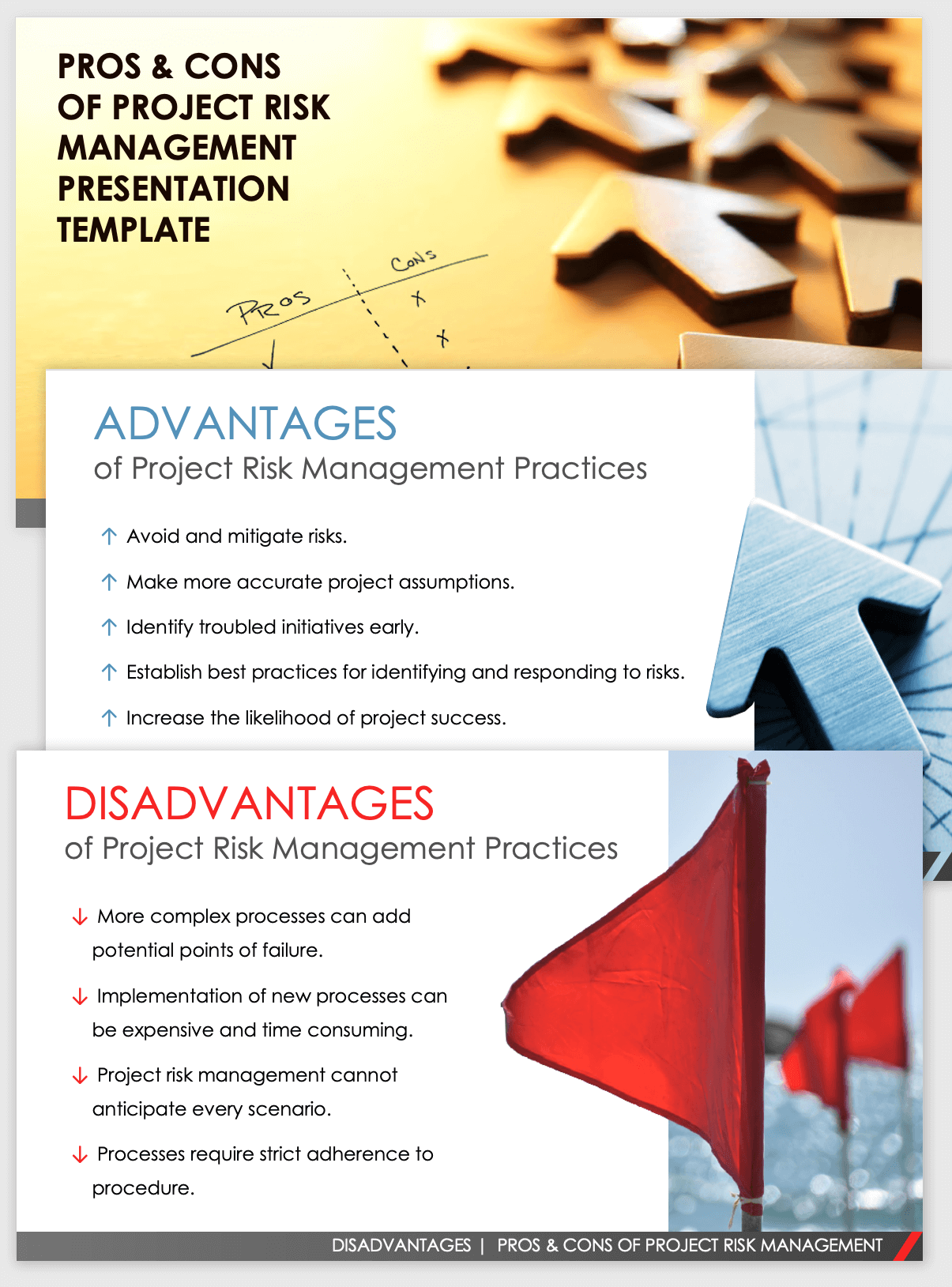
It internet makes it possible for smooth process and combinations and lowers ineffectiveness. It provides top-tier security functions to safeguard delicate data. This risk administration software program is a perfect tool for centers wanting to repair unnecessary concerns or threats. It comes with numerous kinds of attributes that make it specific for ERM managers. Here we have highlighted a few of its crucial functions for your advantage, so take an appearance.
Users can also utilize the AI-powered tools and pre-existing material to produce, assess, prioritize, and address threats successfully. Simplifies the process of configuring and inhabiting threat signs up. Makes use of AI and collection material to boost danger evaluation accuracy. It enables faster my website recognition and reduction of threats, This is mostly an aesthetic model.